Which is the greater danger, a single tipsy call to an ex-girlfriend or a ranting blog post that gets syndicated?
Seems there is an opportunity for a social aspect.
Before a post can go live you need to get 2 out of 3 sign-offs from your designated 'review friends'.
The dynamic of a friend saying "C'mon, you don't really want to do this" has saved many a real-world reputation.
Just pick your friends carefully. As always a judicious balance of cautious conservatism and don't give a sh$t would be appropriate.
When you don't have anything nice to say, well then perhaps its time consider a career as an analyst.
Friday, June 30, 2006
Wednesday, June 28, 2006
PeopleAggregator Authentication Woes
I'm trying to play around with the PeopleAggregator alpha.
PeopleAggregator offers multiple options for logging in.
When I tried to use my mudman.videntity.org OpenID identity I saw this error message from Videntity
When using Flickr, I see a consent message as shown.
 So somebody named Test(or is it Phil) wants permission to show me MY pictures?
So somebody named Test(or is it Phil) wants permission to show me MY pictures?
After giving 'Phil' what he wants I'm successfully logged in.
When I then attempt to modify my PA profile I see the second pic.
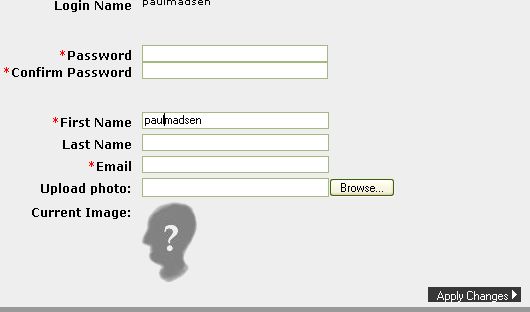
But, I used Flickr to log in so that I wouldn't be required to provide a password? Despite the password being indicated as required info for the profile, I was able to save changes.
After logging out, I then tried to log in again using the same Flickr identity. I see
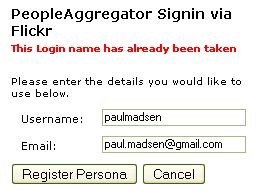
So now it seems I can't delete this profile.
When I created another profile (using a local account name and password) I saw to my surprise that Marc Canter was automatically added as a 'relation' of mine. I have never met Marc so this isn't some incredibly insightful matching engine. This does help to explain why he is already at 126 relations for himself.
Some of these issues have nothing to do with PeopleAggregator. Some are of course because PeopleAggregator is alpha and so will have bugs to be fixed. The interesting ones hilite how difficult it will be to build an experience to explain/convince/assuage the public in Peoria why the fact that they don't have to provide a password is a good thing.
PeopleAggregator offers multiple options for logging in.
When I tried to use my mudman.videntity.org OpenID identity I saw this error message from Videntity
openid.mode:error openid.error:Malformed trust_rootNo prob, I have others. When I tried my mudman.pip.videntity.org OpenID identity I saw this from Verisign
Application Error - Sorry, it appears that you have found a bug. Our developers have been notified and are at work to correct the situation.Running out of options, Flickr was next.
When using Flickr, I see a consent message as shown.
 So somebody named Test(or is it Phil) wants permission to show me MY pictures?
So somebody named Test(or is it Phil) wants permission to show me MY pictures?After giving 'Phil' what he wants I'm successfully logged in.
When I then attempt to modify my PA profile I see the second pic.

But, I used Flickr to log in so that I wouldn't be required to provide a password? Despite the password being indicated as required info for the profile, I was able to save changes.
After logging out, I then tried to log in again using the same Flickr identity. I see

So now it seems I can't delete this profile.
When I created another profile (using a local account name and password) I saw to my surprise that Marc Canter was automatically added as a 'relation' of mine. I have never met Marc so this isn't some incredibly insightful matching engine. This does help to explain why he is already at 126 relations for himself.
Some of these issues have nothing to do with PeopleAggregator. Some are of course because PeopleAggregator is alpha and so will have bugs to be fixed. The interesting ones hilite how difficult it will be to build an experience to explain/convince/assuage the public in Peoria why the fact that they don't have to provide a password is a good thing.
Tuesday, June 27, 2006
Get six-pack ads!
PersonalsTrainer advises the love lorn on how to firm up their personal ads
You know what you want to say, but sometimes the words just don't come out right. We can help. Get a brand-new custom-written profile in your own voice, and see what a difference it can make.Would this be 3rd party or self-asserted identity?
For phishers with limited HTML skills
Sunday, June 25, 2006
Recall of Faulty Identity Selector?
The Inquirer reports on the explosion of a laptop at a 'Japanese conference'.
My source informs me that it was the recent OMA conference in Osaka, it was a meeting on push-to-talk over cellular, and that nobody was hurt.
Rumour has it that the unlucky attendee was using an pre-beta identity selector to share their sushi preferences with a local restaurant.
My source informs me that it was the recent OMA conference in Osaka, it was a meeting on push-to-talk over cellular, and that nobody was hurt.
Rumour has it that the unlucky attendee was using an pre-beta identity selector to share their sushi preferences with a local restaurant.
Friday, June 23, 2006
Personal QR Codes
 This blog URL converted into a QR code.
This blog URL converted into a QR code.Of course, the conversion tool could be saying anything they want about me. I don't have a phone capable of reading it.
Maybe I could listen to it instead.
Thursday, June 22, 2006
Tuesday, June 20, 2006
Cardspace & the local IDP
I've read a number of times (but can't find references) that Microsoft doesn't see the locally hosted IDP as the primary one, but that rather they still expect most identity to come from trusted 3rd party IDPs. I've seen the local IDP described as 'for testing' or 'to get things rolling' etc. Makes sense, self-asserted identity has its limitations.
But, now I see Kim Cameron reference a Mike Beach post (or comment?) with the following
My interpretation of Mike's description above is that some TTP asserts (and thereby provide the authoritative identity) but the claim then gets cached by Cardspace for later presentation to a RP (the 'give it to the user for safe keeping'). This scenario would appear to be neither the (what I assume to be the default) flow of identity assertion created (at run time) and sent by the trusted 3rd party IDP to Cardspace for forwarding onto the RP, nor a self-assertion created by the local IDP.
Just when I thought I was understanding .....
But, now I see Kim Cameron reference a Mike Beach post (or comment?) with the following
This doesn't jibe with what I know (or misunderstand) of Cardspace.
In the privacy space a colleague of my shared an interesting perspective. Most corporations, especially in the B2C space, have considered user/customer identity data to be an asset. Knowledge about their users that could be leveraged for any number of marketing opportunities. With the rising concerns and increasing regulations around privacy this perspective is, or should be, starting to change. This “asset” is now becoming a liability. Data about people (corporate people and consumer people) is always going to be required to do business, but how do we get that while at the same time minimizing liability? Enter the Infocard concept. It would seem we now have a means to establish authoritative data about the user, but give it to the user for safe keeping.(emphasis mine)
My interpretation of Mike's description above is that some TTP asserts (and thereby provide the authoritative identity) but the claim then gets cached by Cardspace for later presentation to a RP (the 'give it to the user for safe keeping'). This scenario would appear to be neither the (what I assume to be the default) flow of identity assertion created (at run time) and sent by the trusted 3rd party IDP to Cardspace for forwarding onto the RP, nor a self-assertion created by the local IDP.
Just when I thought I was understanding .....
The Power of Context
Somebody named 'Pamela' left an insightful comment (in addition to that of Gerald) to a previous post of mine on the workings of Microsoft Cardspace.
Without the obvious experience and insight into Cardspace demonstrated by the commenter, I wouldn't have thought to search by combining her name and the qualifier 'identity'.
It's still only a guess but I'm pretty optimistic that the third hit down is the right one.
Adding a Canadian like Pam to Whodentity would skew the North American identity distribution just that little bit more towards the 49th (as was pointed out to me by Dave in a comment to a different post).
Without the obvious experience and insight into Cardspace demonstrated by the commenter, I wouldn't have thought to search by combining her name and the qualifier 'identity'.
It's still only a guess but I'm pretty optimistic that the third hit down is the right one.
Adding a Canadian like Pam to Whodentity would skew the North American identity distribution just that little bit more towards the 49th (as was pointed out to me by Dave in a comment to a different post).
Ownership claim mechanisms
A post on the Identity Trail, and my recent experiments with ClaimID's verification mechanism made me think about the general question of "How do I convince somebody that some online resource is mine"?
Related but different, which of the above mechanisms would serve to convince that an identity resource is 'about' me? The second, third and last options would appear to be excluded.
- By having the resource in my 'possession' (and the RP having some expectation that such possession is restricted)
- By making a modification (at the behest of the RP) to the resource
- By demonstrating my ability to control access to the resource
- By demonstrating knowledge of some secret associated with the resource
- By having a trusted 3rd party (or lots of somewhat trusted 3rd parties?) assert to my ownership of the resource
- By responding to a challenge message sent to the address of the resource
Related but different, which of the above mechanisms would serve to convince that an identity resource is 'about' me? The second, third and last options would appear to be excluded.
Dial 'N' for NoSig
 Jeff Hodges & Scott Cantor have created a proposal for a new SAML Binding - most notable for its optional use of XML Signature.
Jeff Hodges & Scott Cantor have created a proposal for a new SAML Binding - most notable for its optional use of XML Signature.Jeff's description for the SSTC was
The central thesis is that for various implementation and deployment scenarios, reliance upon XMLdsig is an inhibitor.I think of this binding as the SAML community turning down the security dials on the protocols (or more accurately ensuring that they can be turned down in an interoperable manner) - lower settings appropriate in some situations.
I don't know just how much effort was expanded by Scott & Jeff on this work - I do know that far more would have been required to be "adding" security at this point.
As is true for haircuts - you get into trouble if you take too much off the first time.
UPDATE - Pete Rowley reminds me that hair grows back. Pete, you obviously have a fine head of hair - I myself am working through what my wife refers to as a 'Kramer period'. Nevertheless, I think we should remain sensitive to the security entitlements of those less fortunate than ourselves.
And with respect to my hairdressing ambitions, I worked through those in my university days cutting my own hair in the mirror to save beer money. As for identity, sometimes its better to delegate to a professional.
Monday, June 19, 2006
A protocol for the people
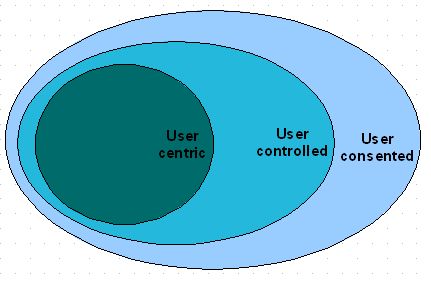 Pete Rowley presents a nice pithy descriptor for user-centric identity - based on the idea that the prime (sole?) criteria for an identity flow to warrant the term is that it occur 'through' the user - and so Pete suggests 'people in the protocol'.
Pete Rowley presents a nice pithy descriptor for user-centric identity - based on the idea that the prime (sole?) criteria for an identity flow to warrant the term is that it occur 'through' the user - and so Pete suggests 'people in the protocol'.Works for me. This is consistent with a taxonomy that some Liberty folks have been bandying about - as shown in the diagram.
The idea is that such user-mediated flows are a subset of a broader category in which the user will still have the ability to specify policy and preferences for how their identity is shared, but would not directly mediate any such sharing. Identity would flow by some other route than through the user, but still determined (at least partially) by the user's own policies. In the diagram, these deployments are labelled as "user-controlled" to capture this different level of control compared to the user-centric case.
Such user-controlled scenarios are themselves a subset of more general user-consented scenarios in which the user may not be given the option for specifying their own policies for how their identity is shared - enterprise use cases being an example. Although the user may not be in control, the assumption is that they have still been given the opportunity to give their consent, even if only through their signature on their employment contract.
Additionally:
- User-centric (as typified by the channel by which identity flows) enables but does not guarantee that the user have the final say on the sharing of their identity. I'm sure that enterprise deployments of Cardspace will support administrative policy that will override any preferences the employee user might have over what cards get presented to which RPs.
- Some identity architectures support only the user-centric flows, and do not allow for the user-controlled flows. But many important identity use cases have one of both subjects offline and thereby unavailable to act as a conduit for the flow of their identity. Does the world stop when I'm not sitting in front of a browser?
- User-centric flows are often described as decoupling the RP and the IDP, and thereby supporting cases where neither need 'know' the other beforehand - this leading to 'scale'. While true in principle, in practice there are lots of other factors pushing the two providers towards each other (such as the realities of risk management) that are independent of the specific channel by which the identity flows. So, if the nature of the shared identity or the value of the transaction doesn't require/imply that the two providers 'know' each other, then it can make sense to share identity through a provider-obfuscating user-centric flow. If not, then the value of the user-mediation is diminished.
Any club that would have me ...
Would you link to a list of purported notables that excluded you? Me neither.
Notwithstanding the few exceptions, the geographic weighting of the list makes me hope that the rest of the world will be happy with the identity systems the States provide us.
Separately, it would be interesting to see the relationships (e.g. corporate partnerships, shared specification development, farm equipment riding, etc) that exist between the list members captured and then visualized.
What topoology does identerati space have? To what extent do these relationships (postive and/or negative) impact identity progress?
Notwithstanding the few exceptions, the geographic weighting of the list makes me hope that the rest of the world will be happy with the identity systems the States provide us.
Separately, it would be interesting to see the relationships (e.g. corporate partnerships, shared specification development, farm equipment riding, etc) that exist between the list members captured and then visualized.
What topoology does identerati space have? To what extent do these relationships (postive and/or negative) impact identity progress?
Friday, June 16, 2006
Top 10 quotes about authority
10) "Authority without wisdom is like a heavy ax without an edge, fitter to bruise than polish" - Anne Bradstreet
9) "Authority is quite degarding" - Oscar Wilde
8) "“There will never be a really free and enlightened State until the State comes to recognize the individual as a higher and independent power, from which all its own power and authority are derived, and treats him accordingly”" - Henry David Thoreau
7) "The ultimate authority must always rest with the individual's own reason and critical analysis." - Dalai Lama
6) "We know, on the authority of Moses, that longer than six thousand years the world did not exist" - Martin Luther
5) "When you make your peace with authority, you become authority." - Jim Morrison
4) "Anyone who conducts an argument by appealing to authority is not using his intelligence; he is just using his memory" - Leonardo Da Vinci
3) "No statement should be believed because it is made by an authority" - Robert Heinlein
2) "All authority belongs to the people" - Thomas Jefferson
and the #1 quote about authority is ...
1) "“To punish me for my contempt for authority, fate made me an authority myself.”" - Albert Einstein
9) "Authority is quite degarding" - Oscar Wilde
8) "“There will never be a really free and enlightened State until the State comes to recognize the individual as a higher and independent power, from which all its own power and authority are derived, and treats him accordingly”" - Henry David Thoreau
7) "The ultimate authority must always rest with the individual's own reason and critical analysis." - Dalai Lama
6) "We know, on the authority of Moses, that longer than six thousand years the world did not exist" - Martin Luther
5) "When you make your peace with authority, you become authority." - Jim Morrison
4) "Anyone who conducts an argument by appealing to authority is not using his intelligence; he is just using his memory" - Leonardo Da Vinci
3) "No statement should be believed because it is made by an authority" - Robert Heinlein
2) "All authority belongs to the people" - Thomas Jefferson
and the #1 quote about authority is ...
1) "“To punish me for my contempt for authority, fate made me an authority myself.”" - Albert Einstein
What's the identity analogy?

The pic is my (poor) attempt at PC trompe l'oeil.
Far better examples of the art can be found here.
There must be an analogy for identity.
A fake persona presented as real?
Or a real persona presented as fake?
Or a real persona presented as a fake persona purporting to be real?
Thursday, June 15, 2006
Sun vows they will not use SAML!
Well at least that was my first thought when I read Eve's news of Sun's "non-assertion covenant".
The truth is better.
I wish I had some IP in SAML so I could join the party.
The truth is better.
I wish I had some IP in SAML so I could join the party.
Tuesday, June 13, 2006
XHTML as a schema language?
Microformats is the philosophy of leveraging existing XHTML structures for markup, rather than defining completely new XML grammars.
As an example, the XML Friends Network (XFN) microformat builds on the XHTML <a> element and uses the "rel" attribute to express the nature of the relationship represented by the HTML link.
There definitely is something to be said for microformats as an end-of-line presentation format - everybody already has a viewer.
But, using XHTML Definition Lists (<DL> elements) to express constraints on the allowed values for the rel attribute (as is proposed here and explained here) seems a perversion.
As an example, the XML Friends Network (XFN) microformat builds on the XHTML <a> element and uses the "rel" attribute to express the nature of the relationship represented by the HTML link.
There definitely is something to be said for microformats as an end-of-line presentation format - everybody already has a viewer.
But, using XHTML Definition Lists (<DL> elements) to express constraints on the allowed values for the rel attribute (as is proposed here and explained here) seems a perversion.
Google Browser Sync
I'm liking the Google Browser Sync extension for Firefox.
Its doing a nice job of keeping my bookmarks (but not other browser settings) synchronized across two laptops. I had previously been experimenting with Foldershare for syncing the "bookmarks.html" file.
I can see this model of server-mediated sycnchronization being useful for some sorts of identity info. Everytime I start up the browser, it would go out to the IDP server, retrieve updated identity and then cache it for (possible) later use at SPs.
If not ruled out by the nature of the identity, or the need for authoritative data, the IDP wouldn't necessarily know if and when the browser subsequently presented the identity to SPs.
As clients get smarter, devices and 3rd party identity provider can work together on the user's behalf in these sorts of interactions. Grossly oversimplifying, its enabling this style of coperation that is the focus of the next phase of Liberty's architecture.
Its doing a nice job of keeping my bookmarks (but not other browser settings) synchronized across two laptops. I had previously been experimenting with Foldershare for syncing the "bookmarks.html" file.
I can see this model of server-mediated sycnchronization being useful for some sorts of identity info. Everytime I start up the browser, it would go out to the IDP server, retrieve updated identity and then cache it for (possible) later use at SPs.
If not ruled out by the nature of the identity, or the need for authoritative data, the IDP wouldn't necessarily know if and when the browser subsequently presented the identity to SPs.
As clients get smarter, devices and 3rd party identity provider can work together on the user's behalf in these sorts of interactions. Grossly oversimplifying, its enabling this style of coperation that is the focus of the next phase of Liberty's architecture.
Infocard to Cardspace
With the name change, what happens to all the blog posts tagged with the old name?
Technorati gives 190 hits for 'cardspace' ; over 2900 for 'infocard'.
Are there no 'bridging mechanisms' to prevent bloggers from having to retroactively change the occurences of the old tags in every impacted post?
Perhaps there is a market for a hosted STS (Switch Tag Service) to enable interoperability.
Technorati gives 190 hits for 'cardspace' ; over 2900 for 'infocard'.
Are there no 'bridging mechanisms' to prevent bloggers from having to retroactively change the occurences of the old tags in every impacted post?
Perhaps there is a market for a hosted STS (Switch Tag Service) to enable interoperability.
Monday, June 12, 2006
DIY-centric geolocation
Real time world cup hilites
My colleague Yuzo Koga is currently flying over the Pacific on his way to Catalyst to give a demonstration of Liberty's People Service.
Between this site and my IM alerts he is able to track the status of the Japan-Australia World Cup match from seat 19D.
Japan leads 1-0 at half time.
Between this site and my IM alerts he is able to track the status of the Japan-Australia World Cup match from seat 19D.
Japan leads 1-0 at half time.
What's the big deal?
There are lots of ring tunes that only adults would be able to hear (e.g. 'Your room is a pigsty - get up there and clean it' or 'Didn't I tell you not to pick that?') so I don't see what the fuss is about.
Sunday, June 11, 2006
Gambare Nippon!
 I expect the Canadian team was excluded on some technicality (i.e. games won etc).
I expect the Canadian team was excluded on some technicality (i.e. games won etc). Regardless I have a worthy replacement team to cheer for.
ClaimID Claims
I've been playing around with ClaimID for a bit. I've found a few references to myself around the Web, and 'claimed' them (and verified those that I can) into my ClaimID collection.
Given stories like this, something like ClaimID seems relevant (in the absence of digital discretion).
ClaimID describes itself:
I can see how it would work if I was able to guide people. I could add my ClaimID URL to my business card or email signature and it would be the starting point from which interested parties would explore.
But this isn't the search scenario that they describe. It's not clear to me how you add this identity contextual layer to the search engines without their buy in. For ClaimID to be valuable, I need to ensure that searchers see my ClaimID explanation of that (shall we say experimental) picture of me at Burning Man before the picture itself - what good is metadata if it can't be found, displayed, integrated etc. At least currently, when I search for myself, I don't see my ClaimID page.
Does ClaimID buy a sponsored link? Or would each link have a ClaimID icon inserted beside it. Sounds like a cool application of a GreaseMonkey script (except you'd have to stipulate on your resume/business card 'Before searching for me please install this script into your browser'.)
Or do you rely on the search indexing algorythms? If I add the ClaimID URL to every page I can touch, will that ensure it rises in the hit ranks?
By the by, the description of MicroID (the mechanism by which I can verify ownership of a link) seems a stretch
Given stories like this, something like ClaimID seems relevant (in the absence of digital discretion).
ClaimID describes itself:
I see ClaimID as allowing me to add a layer of metadata about (or to) existing Web references to myself, and thereby ensure that they won't be missed (the good ones) or misinterpreted (the bad ones) by anyone who happened to be searching for me.
ClaimID is a service that lets you claim the information that is about you online. That information is then associated with your name, providing folks an easy way to see what is and isn't about you online. In doing so, you get to influence the search engines, and provide people more relevant information when they search for you. It's time to reclaim some power back from the search engines. ClaimID is about letting you have some say in what search engines say about you.
I can see how it would work if I was able to guide people. I could add my ClaimID URL to my business card or email signature and it would be the starting point from which interested parties would explore.
But this isn't the search scenario that they describe. It's not clear to me how you add this identity contextual layer to the search engines without their buy in. For ClaimID to be valuable, I need to ensure that searchers see my ClaimID explanation of that (shall we say experimental) picture of me at Burning Man before the picture itself - what good is metadata if it can't be found, displayed, integrated etc. At least currently, when I search for myself, I don't see my ClaimID page.
Does ClaimID buy a sponsored link? Or would each link have a ClaimID icon inserted beside it. Sounds like a cool application of a GreaseMonkey script (except you'd have to stipulate on your resume/business card 'Before searching for me please install this script into your browser'.)
Or do you rely on the search indexing algorythms? If I add the ClaimID URL to every page I can touch, will that ensure it rises in the hit ranks?
By the by, the description of MicroID (the mechanism by which I can verify ownership of a link) seems a stretch
A MicroID is a standards-based way to "claim" a page that you have authored.
Friday, June 09, 2006
Sub-urban Legend?
Identity Woman is up in arms about the possibility of her cell number being released to marketers.
I would be as well ... if it were true.
A quick google of the purported 'do not call' number of '888-382-1222' found this.
I would be as well ... if it were true.
A quick google of the purported 'do not call' number of '888-382-1222' found this.
Those damn Danes!
Can't fight the numbers
Nokia commisioned a survey on how people use their cells now, and how they want to use them in the future. The results are interesting
- 44% use their mobile device as their primary camera, with India being home to the most prolific mobile photographers (68%).
- Globally, seventy two percent now don't use a separate alarm clock and 73% use their mobile as their main watch or clock.
- 36% of respondents are browsing on their mobile devices at least once a month. Japan leads the way in mobile internet usage with 37% admitting to going online on their mobile on a daily basis.
- 94% of those questioned plan to have a mobile in the future. People in Brazil love mobiles so much that 100% believe they'll own a mobile device in years to come.
- 21% would be more upset about losing their mobile than their wallet, credit cards and even their wedding ring.
- 67% predict the mobile phone will replace their MP3 player.
- 42% of respondents globally want their printer, PC, stereo, TV and mobile device interconnected.
- 58% of those questioned would like to be able to control all their household appliances via their mobile device.
MyStalk
DatingAnyone allows people to track the dating status (e.g. single, swinger, in a relationship) of particular MySpace members, and be notified if and when it changes.
Their bot trawls only publicly available information, the same as would be available by browsing the MySpace Web interface. The MySpace profile also includes smoking & drinking habits - how long before the respective lobbying organizations for these two industries start to harvest and leverage the availability of this info - the demographics are right.
Their bot trawls only publicly available information, the same as would be available by browsing the MySpace Web interface. The MySpace profile also includes smoking & drinking habits - how long before the respective lobbying organizations for these two industries start to harvest and leverage the availability of this info - the demographics are right.
Google - buying my identity one piece at a time
A sea of acronyms
Darryl sent along the following list of acronyms (some freshly minted) that we used in a recent Liberty meeting:
WSC, TM, TMA, WSP, DS, IdP, IETF, HTTP, REL, SP, SAML, MED, MING, AOL, PIS, PISID, SSO, MRD, PSTN, IS, SSL, SSN, CDR, Radius, XCap, iClient, TMM, URI, DAA, DMS, IABT, PPCSU, MCSU, MCPCSU, MBT, LUAD, BMEG, WTF, WSF, AS, SASL, SSTC, MINGED, PAOS, AIM.
I was there and have no idea of what some of these represent.
I do remember 'WTF' was particularly popular as we reviewed a requirements document.
WSC, TM, TMA, WSP, DS, IdP, IETF, HTTP, REL, SP, SAML, MED, MING, AOL, PIS, PISID, SSO, MRD, PSTN, IS, SSL, SSN, CDR, Radius, XCap, iClient, TMM, URI, DAA, DMS, IABT, PPCSU, MCSU, MCPCSU, MBT, LUAD, BMEG, WTF, WSF, AS, SASL, SSTC, MINGED, PAOS, AIM.
I was there and have no idea of what some of these represent.
I do remember 'WTF' was particularly popular as we reviewed a requirements document.
Anonymous air travel
On a dare, Jim Harper makes it through security at SFO without presenting any identification.
Notwithstanding the signs asserting that identification MUST be shown for flying in the US, it seems that the real policy is a MAY - either show some approved id or submit to more extensive searches. So, prove your verinymous identity, or stay anonymous but otherwise demonstrate you pose no risk.
I guess the computing parallel would be to be granted root privileges after proving you have no programming ability. I'm in.
Notwithstanding the signs asserting that identification MUST be shown for flying in the US, it seems that the real policy is a MAY - either show some approved id or submit to more extensive searches. So, prove your verinymous identity, or stay anonymous but otherwise demonstrate you pose no risk.
I guess the computing parallel would be to be granted root privileges after proving you have no programming ability. I'm in.
Wednesday, June 07, 2006
Tenuous Connection to Identity
Seed magazine reports that researchers have discovered a connection between genetics and human sexual behaviour. Shocking news!
Given that our sexual behaviour is the mechanism (though not the only possible one) by which our genes reproduce themselves - it would be very surprising were sexual behaviour (like many others aspects of our social interactions) not genetically linked to some extent.
Does beg the question, how can a genotype that leads to a low sex-drive phenotype persist and not be selected out? All else being equal, somebody with a low sex-drive will be less likely to have descendants than somebody else with normal or high levels of 'horniness'. Fewer descendants means that fewer copies of the gene will survive. I expect that the horniness gene is somehow linked to another whose advantages can outweigh this effect.
As justification for a post on genetics & sexuality here, I point to a currently (long) running thread on the ID Gang list on the applicability and issues of DNA as a biometric.
Given that our sexual behaviour is the mechanism (though not the only possible one) by which our genes reproduce themselves - it would be very surprising were sexual behaviour (like many others aspects of our social interactions) not genetically linked to some extent.
Does beg the question, how can a genotype that leads to a low sex-drive phenotype persist and not be selected out? All else being equal, somebody with a low sex-drive will be less likely to have descendants than somebody else with normal or high levels of 'horniness'. Fewer descendants means that fewer copies of the gene will survive. I expect that the horniness gene is somehow linked to another whose advantages can outweigh this effect.
As justification for a post on genetics & sexuality here, I point to a currently (long) running thread on the ID Gang list on the applicability and issues of DNA as a biometric.
Tuesday, June 06, 2006
Top-down eh!

I'm reading Pierre Burton's The Last Spike - his history of the building of the Canadian Pacific Railway.
The construction camps for the road were 'dry'. In a chapter on the effect of prohibition on the construction of the railway, Burton writes:
Lively they were, and never entirely dry, but the prairie railway camps, in contrast to those south of the border, were relatively tame. The contractors, American and Canadian, were grateful. "When a man breaks the law here", one American boss told George Grant, "justice is dealt to him a heap quicker and in larger chunks than he has been accustomed to in the States. I tell you there is a way to do it, and they are doing it here, right from scratch". What he was praising, of course, was the Canadian passion for order imposed from above - a British colonial heritage - as against the American concept of localized grass-roots democracy. There were no gun-toting town marshalls keeping the peace in the Canadian West; instead there was a federally appointed, quasi-military constabulary. The Mounties did not have to stand for election, they were relatively incorruptible, and they were fair; that was one of the reasons why the Canadian West lacked some of the so-called colour of its American counterpart.
I'm just glad Liberty receptions aren't dry. Train engines need to be kept lubricated.
p.s. Extra credit exercise - write a 5-page essay on "Railway gauges and their competitive application". Avoid the use of 'de facto' for bonus marks.
Monday, June 05, 2006
No animals were harmed in the manufacture of this token
 Cleaning up a neighborhood road with family & friends, we took out 22 bags of garbage. We also took out a single RSA SecurID token previously belonging to an employee of a prominent local IT company (likely stolen and then tossed into the woods once the thief realized it wasn't a garage door opener).
Cleaning up a neighborhood road with family & friends, we took out 22 bags of garbage. We also took out a single RSA SecurID token previously belonging to an employee of a prominent local IT company (likely stolen and then tossed into the woods once the thief realized it wasn't a garage door opener).The token has an URL on its back, at which there are instructions for anybody who comes across a token.
Fundamentally, the guidance is 'toss it'. Presumably to convince finders of the environmental sanctity of this course of action, RSA provides a reassuring Token Disposal Statement.
- No hazardous materials are used in the manufacture of the product. The products contain no CFCs or ozone depleting materials, nor were such materials used in their manufacture.
- RSA SecurID tokens are lead free, and use a low voltage 3.3 volt lithium battery. When new, a token has less than .5 grams of lithium. This amount decreases as the token is used. This amount is very small and does not pose any health risk.
- RSA SecurID tokens are also completely emission free, and do not emit radiation or electro-magnetic waves.

Notwithstanding the above assertion, potential emissions would appear to be yet another downside of the 'token necklace' phenomena (I wonder if I should shorten the length of my Token Neck Strap (TNS) to ensure that any such emissions penetrate harmlessly into my upper thorax rather than genetically sensitive alternatives?). Or, might the emissions of multiple tokens cancel each other? Do I need more tokens arranged strategically around my body?
Personally, I think RSA could have done more to encourage recycling.
If found, this SAML assertion makes a nice greeting card when printed out.
Sunday, June 04, 2006
Big in Japan
Big in Japan is a cool set of Web 2.0 tools.
I wish I could say I came across the site while ego surfing.
I wish I could say I came across the site while ego surfing.
Saturday, June 03, 2006
Eats Shrimp and Leaves
Punctuation can be critical. Johannes inserts a trailing "?" and a hyphenated "un" in the title of his post and is able to pack some heavy semantics (my interpretation at least) into a short name.
Presumably the "un" is meant to indicate that Liberty sponsoring an event in partnership with IIW is somehow out of character, and unlike what he would have expected of Liberty's organizational behaviour. It's either that or Liberty is super cool, like the Un-cola (or LID is, or whatever).
The final question mark is even more meaningful - it allows Johannes to imply a certain level of skepticism about the motives of Liberty (perhaps IIW as well) for taking this step (or perhaps questioning whether it is indeed unlike Liberty in the first place). All in all, a skilfully created title with multiple rich interpretations introduced by the punctuation (and not negated by the later support Johannes shows for the event in the body of his post I think).
So punctuation can be key, and not just in altering textual semantics. The evolutionary biologists Stephen Jay Gould and Niles Eldridge developed a theory of evolutionary change in which the normal state of affairs for sexually reproducing species is stasis, i.e. most of the time they are not evolving in any appreciable manner but merely coasting along. When change does occur, it happens quickly and unexpectedly - before the system once more settles back into the more typical state (different than before) of stasis. They labelled their theory "punctuated equilibria" to characterize this pattern of long periods of sameness punctuated by infrequent periods of upheaval.
I highly doubt that the outcome of the IIW/Liberty Identity Open Space event will be a converged identity metasystem (even were all the players to attend). We will not "evolve" to the metasystem in a single cataclysmic jump as the punctuated equilibria theorists would predict (were they to care). As useful a forum for discussion that "open spaces" might be, and as effective a co-ordinator Kaliya, it will take more than two days of whiteboarding and some socialization over cold shrimp at a reception for convergence (or even harmonization) to happen.
For identity evolution, the track on which we are moving is one of slow and gradual changes - this evolution enabled by greater understanding (both technical and organizational) between all organisms. The Vancouver event will be just one more step along this route.
I do hope no Creation Scientists attend IOS - they always cluster around the bar and you can never get a drink.
Notes:
Presumably the "un" is meant to indicate that Liberty sponsoring an event in partnership with IIW is somehow out of character, and unlike what he would have expected of Liberty's organizational behaviour. It's either that or Liberty is super cool, like the Un-cola (or LID is, or whatever).
The final question mark is even more meaningful - it allows Johannes to imply a certain level of skepticism about the motives of Liberty (perhaps IIW as well) for taking this step (or perhaps questioning whether it is indeed unlike Liberty in the first place). All in all, a skilfully created title with multiple rich interpretations introduced by the punctuation (and not negated by the later support Johannes shows for the event in the body of his post I think).
So punctuation can be key, and not just in altering textual semantics. The evolutionary biologists Stephen Jay Gould and Niles Eldridge developed a theory of evolutionary change in which the normal state of affairs for sexually reproducing species is stasis, i.e. most of the time they are not evolving in any appreciable manner but merely coasting along. When change does occur, it happens quickly and unexpectedly - before the system once more settles back into the more typical state (different than before) of stasis. They labelled their theory "punctuated equilibria" to characterize this pattern of long periods of sameness punctuated by infrequent periods of upheaval.
I highly doubt that the outcome of the IIW/Liberty Identity Open Space event will be a converged identity metasystem (even were all the players to attend). We will not "evolve" to the metasystem in a single cataclysmic jump as the punctuated equilibria theorists would predict (were they to care). As useful a forum for discussion that "open spaces" might be, and as effective a co-ordinator Kaliya, it will take more than two days of whiteboarding and some socialization over cold shrimp at a reception for convergence (or even harmonization) to happen.
For identity evolution, the track on which we are moving is one of slow and gradual changes - this evolution enabled by greater understanding (both technical and organizational) between all organisms. The Vancouver event will be just one more step along this route.
I do hope no Creation Scientists attend IOS - they always cluster around the bar and you can never get a drink.
Notes:
- I make allusions to 'progress' in a discussion of evolution. This is of course bad science. I console myself that I am not the first to rely on a flawed analogy in order to make a point.
- Is a hyphen punctuation? I chose to interpret it so.
- I've never actally met a Creation Scientist so their drinking habits are just a guess.
Friday, June 02, 2006
OpenID for social sharing
Brian Ellin posts about a script he created by which access to resources can be controlled in OpenID.
Brian wanted to share a playlist but didn't want to make it available to all and sundry. This scenario, of one user controlling which of their friends/family/colleagues can access some resource of theirs, was key for the development of Liberty's People Service.
This is the first time I've seen it explored in the context of a URI-based identity system like OpenID. I can see some differences (which may or may not reflect any real architectural differences between OpenID and Liberty):
Differences aside, it's interesting to see different identity systems moving beyond SSO.
Brian wanted to share a playlist but didn't want to make it available to all and sundry. This scenario, of one user controlling which of their friends/family/colleagues can access some resource of theirs, was key for the development of Liberty's People Service.
This is the first time I've seen it explored in the context of a URI-based identity system like OpenID. I can see some differences (which may or may not reflect any real architectural differences between OpenID and Liberty):
- Brian has the 'trust list' (i.e. the list of friends authorized to view the playlist) maintained and running at the service provider at which the resource is hosted. The implication is that he would need to duplicate the creation and management of this list (or some variation) at any other SP at which he has other resources for which this sort of access control would be desired (or even for some other playlist held at the same SP).
The whole premise of the People Service was to pull the management and storage of this sort of 'friends list' away from particular SPs to a dedicated provider. SPs still own the access control policies, but the rules are defined in terms of identities and/or groups held at the dedicated People Service Provider. For the user, the value is maintaining their friends list in one place, but leveraging it all the various SPs that refer to it. Critically, in the People Service, access permissions can be defined against a group of users rather than individual identifiers.
An OpenID-based system could presumably do something similar through retrieval of a centralized FOAF file. - Brian's model for getting people onto the list is
Email me at brianellin at @@@@.com, and I’ll stick you in the trusted list.
So, were you to send Brian a mail requesting access to the playlist, you would supply your Openid URI and Brian would add it to the approved list.
In the People Service, we defined an invitation mechanism by which the resource owner would notify his/her friends of the possibility of being added to the list and the access to some resource that would be enabled, and be given the option of declining the privilege if desired. - The resource here (the playlist) would be accessed through a browser and then downloaded or played.
In support of this sort of cross-principal resource sharing, we added new functionality to Liberty's Web Service Framework so that one user (or some provider acting on that user's behalf) is able to access the identity resources of another (user) through SOAP interfaces and not just the browser.
So, for instance, my music player could retrieve the playlist directly from the hosting server, rather than reply on me to initiate things through the browser. Also possible would be for me to be given appropriate rights so that my client could post my own playlists to the server through the same APIs.
Differences aside, it's interesting to see different identity systems moving beyond SSO.
Steganography alive and well in China
The Chinese refer to Tiananmen Square Massacre as 6489 (June 4, 1989).
I was just reading a Chinese blogger and was initially confused by the occurence of strings such as June 1234, 3149683659.
I wonder if the numeric identifier was chosen because of the ease with which it can be embedded in innocent strings and thereby fool the filters.
The blogger also makes use of a variety of obfuscated versions of 'democracy', 'political', 'censored' etc. Can't help but think though that filters could be tuned to watch for 'Ti@@@@@@@en Square'.
I was just reading a Chinese blogger and was initially confused by the occurence of strings such as June 1234, 3149683659.
I wonder if the numeric identifier was chosen because of the ease with which it can be embedded in innocent strings and thereby fool the filters.
The blogger also makes use of a variety of obfuscated versions of 'democracy', 'political', 'censored' etc. Can't help but think though that filters could be tuned to watch for 'Ti@@@@@@@en Square'.
Thursday, June 01, 2006
Jeopardy vs Millionaire
Lest anybody think Conor and I argue only about matters lacking substance, I've just returned from a wing dinner in which we debated the relative merits of 'Jeopardy' and 'Who Wants to be a Millionaire".
My opening statement can be paraphrased as "The two shows are targetting completely different demographics - Jeopardy is going after viewers with brains, Millionaire isn't so focussed".
Conor, unbeknownst to me, is a big fan of Millionaire (and Regis!) and so seemed to take offense. Neither of was able to convince the other of the error of his ways (much like many TEG chats) through subsequent discussion.
By coincidence, Jeopardy was playing when I got back to the hotel room. Final Jeopardy was:
Conor, are you going to use one of your lifelines?
My opening statement can be paraphrased as "The two shows are targetting completely different demographics - Jeopardy is going after viewers with brains, Millionaire isn't so focussed".
Conor, unbeknownst to me, is a big fan of Millionaire (and Regis!) and so seemed to take offense. Neither of was able to convince the other of the error of his ways (much like many TEG chats) through subsequent discussion.
By coincidence, Jeopardy was playing when I got back to the hotel room. Final Jeopardy was:
"In 2005, Broadway's Virginia Theater was renamed to honour this late author, the first African-American so honoured"I think that pretty much sums it up - the average Millionaire viewer probably thinks "Broadway" is a particularly wide stock car track.
Conor, are you going to use one of your lifelines?
Name Card Lady
A friend of mine (named Ian) sent me the following email.
I had an interesting ID related experience tonight at an event. The lady filling out the name cards asked for my name. I said “My name is Ian. I – A – N”. I then watched as she wrote “ENIAN” on my name card. I politely corrected her and received a new card. In retrospect, I regret not taking the “ENIAN” card. If anyone had asked me the origin of the name I could have simply pointed to the name card lady. Surely, this process would have gone more smoothly if I had a business card to present at the registration table. I can’t help but think the same would be true for web based transactions.I love it when amateurs think they can design identity systems.
- The name by which the Name Card Lady knows me would be the same as that she asserts to the other attendees. GUID
- He misses an obvious acronym opportunity with NCL (Name Card Lady)
- Not a single mention of 'user-centric' or 'metasystem'.
IIW & LAP

IIW and Liberty are teaming up to sponsor an "Identity Open Space" on July 20-21 in Vancouver.
IIW has a wiki.
In addition to this event, Liberty is inviting attendees (even non-members with a signed NDA) to sit in on Liberty's normally scheduled Sponsor meetings directly preceeding (and also in Vancouver at the same location) the Open Space.
Somewhere, a flock of pigs flys gracefully across the sky.
Subscribe to:
Comments (Atom)
