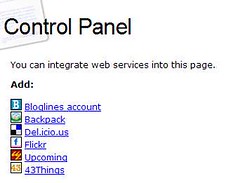
The “six degrees” theory contends that any human being in the world can be “connected” to another human being by a path traceable through about no more than six different people.
Early research suggested that the Web's version of the rule was '19 degress of separation", i.e. that any one Web site is no more than about 19 "clicks” away from any other site.
In 2000 however, IBM, Altavista, and Compaq
discovered that the Web isn't so connected. When you can get from one to another, it's about 19 clicks, but sometimes 'you can't get there from here'.
The connected Web was found to be divided into four parts (their combined shape usually described as a "bow tie")
- the central, highly connected core or knot of the bow tie, where pages have hyperlinks to *and* from other pages in the core
- one section adjacent to the core (one loop of the bow), where pages have hyperlinks into the core pages but not from them
- another section adjacent to the core (the other loop of the bow), where pages have links from the core pages but not into them
- the tendrils (the straps of the bow tie) abutting the loop sections, where pages have links either into pages that have no link into core pages or from pages that have no link from core pages
This topography results from the Web being a
directed graph, connections between nodes have directions. For the Web, its the fact that HTML's <a href=""> mechanism is one-sided.
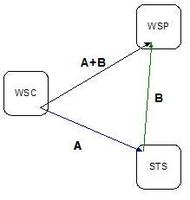
The network created between sites/providers by the fact of some issuing identity tokens (identity providers) and some choosing to rely on them (service providers) is also directed; one site might issue assertions to another but this is not to say that the reciprocal relationship would exist. Additionally, a site might act as an identity provider in some transactions and a service provider for others.
Consequently, I expect there will be a similar "bow tie" topography for the "provider network". By analogy, there should be:
- a strongly connected central knot where it would be possible to jump from any one to another (but not for any one particular user)
- the "IN" loop in which there are identity providers who will issue identity tokens to sites in the central core, but not accept tokens from any in the core (the major portals like AOL)
- the "OUT" loop in which there are service providers who will accept identity tokens from core providers but not issue them (presumably the vast majority of sites)
- islands of isolated CoTs
Given that we are starting with isolated CoTs, it should be interesting to see the network evolve. Islands will be connected together through one CoT member establishing the necessary business agreements with a provider in another CoT.