
Tag Lady points to a interesting decision from the Danish Government.
Makes me proud of my Danish heritage.
When you don't have anything nice to say, well then perhaps its time consider a career as an analyst.


...when rules are kept simple and incentives are provided from the Top-down, the energies of the Bottom can be realized for mutual gain. However, negotiating the sharing of control is both ripe with risk and opportunity.In today's identity, SAML, Liberty, and Infocard are typically presented as top-down initiatives; LID, OpenID, YADIS as bottom-up.

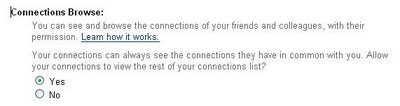
an online business contact marketplace where marketers, recruiters, and sales people can buy, sell and trade business contact informationMembers buy their way in, either through a monthly subscription fee or by providing a certain number of their contacts to the system. Yes, the currency is the contact info of your friends and colleagues.
So today is a milestone for us. It’s the public rollout of these user-centric XML Web services. It is a new model for user-centric computing. This is not the world of cookies and things that are very opaque to users. This is a world of a very explicit schema that you choose how you want to control the different parts of that schema in terms of how you fill in the information and where it is made available.
70509-060414-622231-41
© 2006 All Rights Reserved.
<canvas>
<view y ="30" >
<simplelayout axis="x" spacing="5"/>
<view id="cart" bgcolor="#666699"
height="250" width="125">
<text fgcolor="#FFFFFF"
x="5" y="5" >Available Identities</text>
</view>
<view id="wish" bgcolor="#666699"
height="100" width="125">
<text fgcolor="#FFFFFF"
x="5" y="5" >Chosen Identity</text>
</view>
</view>
<view x="${cart.x+10}" y="${cart.y+55}"
resource="blast.jpg"
onmousedown="dragging.apply()"
onmouseup="dragging.remove();">
<dragstate name="dragging"/>
<method name="stop">
if (this.x>wish.x) {
this.animate("x", wish.x+10, 300);
this.animate("y", wish.y+55, 300);
} else {
this.animate("x", cart.x+10, 300);
this.animate("y", cart.y+55, 300);
}
</method>
</view>
<view x="${cart.x+10}" y="${cart.y+125}"
resource="choo.jpg"
onmousedown="dragging.apply()"
onmouseup="dragging.remove();">
<dragstate name="dragging"/>
<method name="stop">
if (this.x>wish.x) {
this.animate("x", wish.x+10, 300);
this.animate("y", wish.y+55, 300);
} else {
this.animate("x", cart.x+10, 300);
this.animate("y", cart.y+55, 300);
}
</method>
</view>
<view x="${cart.x+10}" y="${cart.y+195}"
resource="astro.jpg"
onmousedown="dragging.apply()"
onmouseup="dragging.remove();">
<dragstate name="dragging"/>
<method name="stop">
if (this.x>wish.x) {
this.animate("x", wish.x+10, 300);
this.animate("y", wish.y+55, 300);
} else {
this.animate("x", cart.x+10, 300);
this.animate("y", cart.y+55, 300);
}
</method>
</view>
<text x="5" y="5">
Drag chosen identity to
</text>
<button x="160" y="150">Select</button>
</canvas>
As part of his "The Story of Digital Identity" podcast series, Aldo Castanada interviewed Ben Adida, a Phd candidate in crypto at MIT.
Ben made one comment in the interview that caught my attention..... everything you do is tied to some kind of identity, at least a pseudonym, because otherwise it's not that useful. I mean, if you go back to Amazon, and Amazon doesn't keep track of anything you do, then it's not a very useful web site ...
Ben seems to be suggesting that Amazon (and other such sites) must necessarily have some sort of persistent pseudonym for users in order to provide them any sort of useful and customized experience.
This ignores the very real potential for anonymous interactions with service providers, where a user's attributes can be asserted by some identity provider as needed, but no persistent account need be maintained at that service provider. Everytime they reappear at the service provider, they see the user fresh (excepting any cookies they might have set on the browser).
Bottom line, service providers will need to know something about you in order to provide differentiated service. Such information could include shipping address, calendar info, reputation etc. Today's reality is that service providers force users to create a credentialed account in order to allow them to track and cumulatively collect such information across multiple visits. But it needn't be this way if the information was supplied as necessary by some other identity provider.
1.a. The act of diverging.
b. The state of being divergent.
c. The degree by which things diverge.
2. Physiology A turning of both eyes outward from a common point or of one eye when the other is fixed.
3. Departure from a norm; deviation.
4. Difference, as of opinion. See Synonyms at deviation, difference.
5. Biology The evolutionary tendency or process by which animals or plants that are descended from a common ancestor evolve into different forms when living under different conditions.
6. Mathematics The property or manner of diverging; failure to approach a limit.
7. A meteorological condition characterized by the uniform expansion in volume of a mass of air over a region, usually accompanied by fair dry weather.

In Adam Nicolson's "God's Secretaries - The Making of the King James Bible" Nicolson portrays the decision by King James I to sponsor a new translation of the Bible as part of his hope to heal the schism within the English Church between conservative Bishops and reforming Puritans. Nicolson suggests that, more than anything else, James Stuart wanted his new reign to be undisturbed by the sort of religious strife that characterized his Scottish upbringing (as evidence his motto 'Blessed are the Peacemakers").
The hope was that a new "authorized version" of the Bible would serve as a middle-ground between the Protestant Geneva Bible (1560) and the established Church of England Bishop's Bible (1568), and thereby settle the many biblical controversies that divided the two camps.
James drafted a set of instructions to the committee of Translators tasked with creating the new version. To one instruction in particular Nicolson assigns particular importance:
No marginal notes at all to be affixed, but only for the explanation of the Hebrew or Greek words, which cannot, without some circumlocution, so briefly and fitly be expressed in the text.

Marginal annotations had been extensively used in the Geneva Bible in order to allow its translators to offer their interpretation and clarification of particular points in the main text (i.e. they profiled the main text). Problem was, King James found most of these clarifications, Calvinistic and Puritan in nature as they were, offensive. Consequently, he instructed that the marginal notes mechanism should be used only sparingly in the new Bible.
Nicolson interprets this instruction to mean that James deliberately sought to ensure that the main text of the new Bible could be, where appropriate, intentionally vague (i.e. underspecified) and unclarified by any marginal notes. For James, such ambiguity in the text would mean that both sides of the dispute, established Church of England Bishops and the reforming Puritans, could find an acceptable interpretation within the new Bible.Where clear direct text had been the goal of the Geneva Bible, the King James Bible would be known for its rich, grand and (importantly) subtle phrasings. Where the Geneva Bible had left no room for any interpretation other than that of its translators and subsequent annotators, the new Bible would provide a rich "platform" on which the different Christian faith systems could build. Bishops and Puritans, while disagreeing on specific interpretations, could agree on the fundamentals as expressed through the text. A meta-bible if you will.
We already have our identity Seven Commandments and evangelists abound. Maybe it's time to consider the Gideon's marketing model in spreading the gospel. I know I spend too much time in hotel rooms.
United States Associate Supreme Court Justice Potter Stewart could have been referring to many things other than pornography when he wrote in an opinion:
I shall not today attempt further to define [obscenity]; and perhaps I could never succeed in intelligibly doing so. But I know it when I see it ...
Hopefully we can do better than this for user-centric identity.
Johannes calls for contributions to the YADIS song.
Note: for optimum enjoyment, this should be sung while wearing motorcycle leathers. Your call of course.
Ya-URL*, there's no need to feel down.
I said, ya-URL, cause your future is sound.
I said, ya-URL, your metadata can now be found
Your issues need not go un-resolv-ed.
Ya-URL, there's a place you can rest.
I said, ya-URL, for your capabilities we can test.
They can start there, and providers can find
Others of a sim-ilar-URI-kind.
It's fun to rest with y-a-d-i-s.
It's fun to rest with y-a-d-i-s.
(Repeat till nauseus)


